- 首页
- 产品
- InsightIDR
- 特性
- Deception Technology
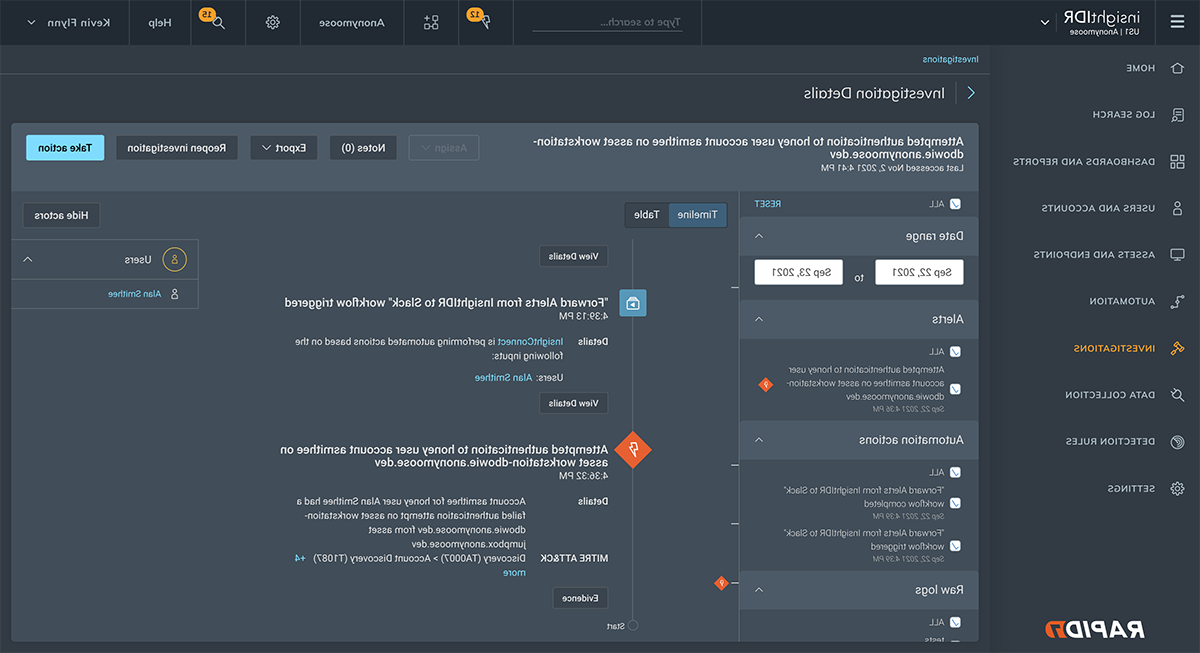
InsightIDR Feature
Deception Technology
Start free trial
No credit card necessary
观看演示
See how it all works
You could slow them down, but let’s just stop them cold
XDR that over-indexes on endpoints or a h和ful of event sources create pores in the environment. You can miss activity that signals something nefarious in play. Attackers can slip by. InsightIDR’s easy-to-deploy deception suite lets you create more traps 和 pitfalls: “粘蜜罐”, 亲爱的用户, honey credentials, 和 honey files - all crafted to identify malicious behavior earlier in the attack chain.